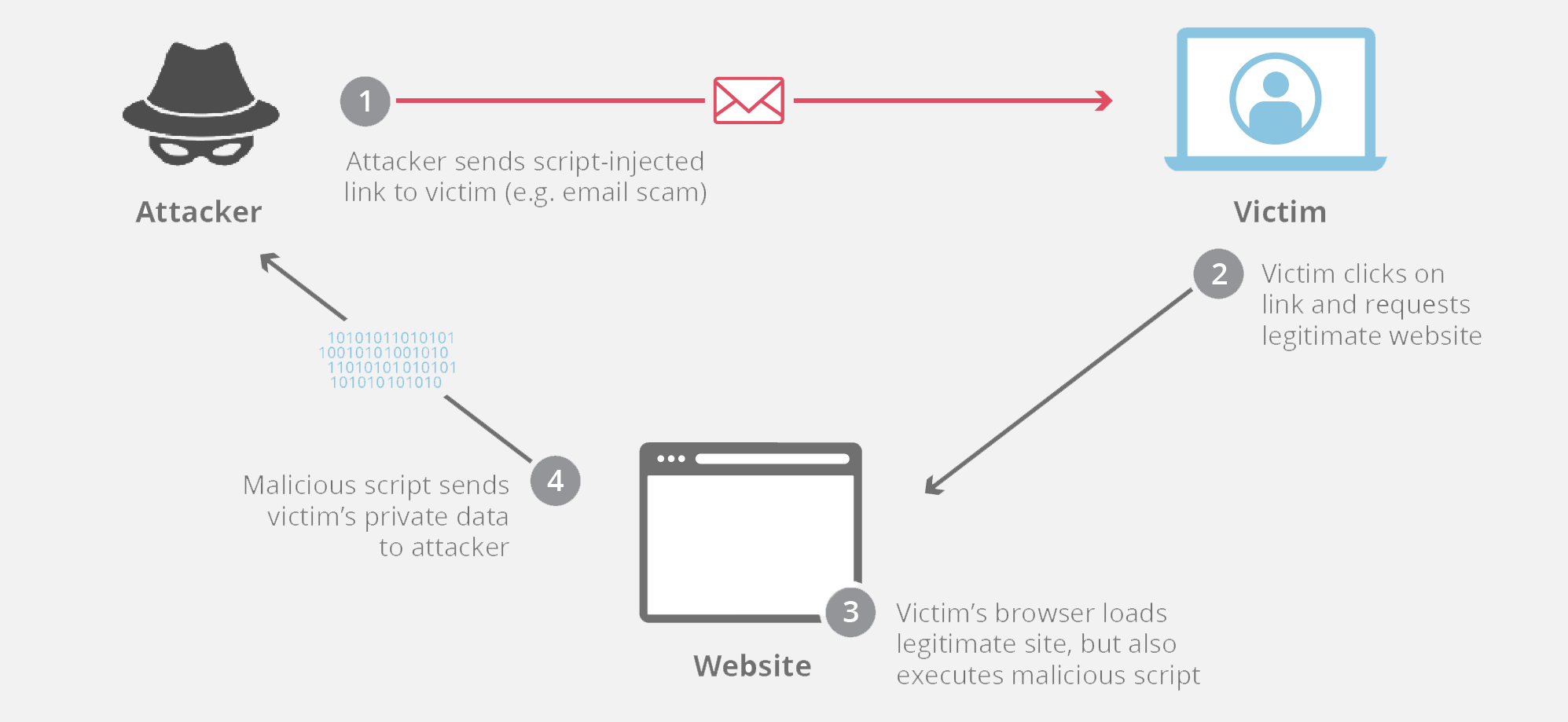
My name is Ismail Tasdelen. As a security researcher. Today I will be talking about how to use an xss vulnerability as a keylogger. After this post, you’ll notice why a xss vulnerability has a critical vulnerability.
|
|
|
|
|
|

My name is Ismail Tasdelen. As a security researcher. Today I will be talking about how to use an xss vulnerability as a keylogger. After this post, you’ll notice why a xss vulnerability has a critical vulnerability.
