washingtonpost.com Cross Site Scripting Vulnerability
Report ID: OBB-687672
Security Researcher MLT
Helped patch 2021 vulnerabilities
Received 5 Coordinated Disclosure badges
Received 1 recommendations
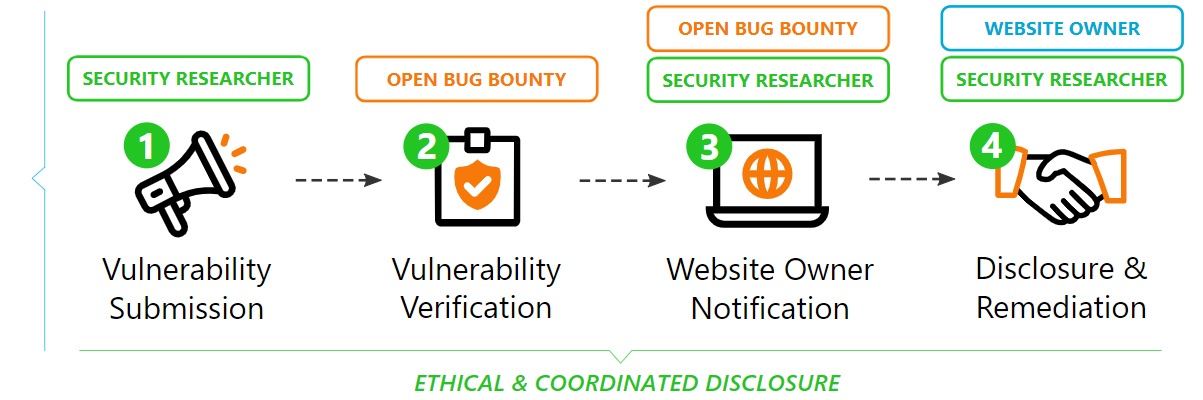
, a holder of 5 badges for responsible and coordinated disclosure, found Cross Site Scripting security vulnerability affecting washingtonpost.com website and its users.
Following the coordinated and responsible vulnerability disclosure guidelines of the ISO 29147 standard, Open Bug Bounty has:
a. verified the vulnerability and confirmed its existence;
b. notified the website operator about its existence.
| Affected Website: | washingtonpost.com |
| Open Bug Bounty Program: | Create your bounty program now. It's open and free. |
| Vulnerable Application: | Custom Code |
| Vulnerability Type: | XSS (Cross Site Scripting) / CWE-79 |
| CVSSv3 Score: | 6.1 [CVSS:3.0/AV:N/AC:L/PR:N/UI:R/S:C/C:L/I:L/A:N] |
| Disclosure Standard: | Coordinated Disclosure based on ISO 29147 guidelines |
| Discovered and Reported by: | MLT
Helped patch 2021 vulnerabilities Received 5 Coordinated Disclosure badges Received 1 recommendations |
| Remediation Guide: | OWASP XSS Prevention Cheat Sheet |
| Export Vulnerability Data: | Bugzilla Vulnerability Data JIRA Vulnerability Data [ Configuration ] Mantis Vulnerability Data Splunk Vulnerability Data XML Vulnerability Data [ XSD ] |
Vulnerable URL:
HTTP POST data:
Mirror: Click here to view the mirror
Coordinated Disclosure Timeline
| Vulnerability Reported: | 18 October, 2018 08:14 GMT |
| Vulnerability Verified: | 18 October, 2018 08:55 GMT |
| Website Operator Notified: | 18 October, 2018 08:55 GMT |
| a. Using the ISO 29147 guidelines |  |
| b. Using publicly available security contacts |  |
| c. Using Open Bug Bounty notification framework |  |
| d. Using security contacts provided by the researcher |  |
| x. Using Twitter notification |  |
| Public Report Published [without technical details]: | 18 October, 2018 08:55 GMT |
| Vulnerability Fixed: | 16 January, 2019 09:15 GMT |
| Public Disclosure: | 17 November, 2018 08:14 GMT |
For Website Operators and Owners
Please read how Open Bug Bounty helps make your websites secure and then contact the researcher directly to get the vulnerability details. The researcher may also help you fix the vulnerability and advice on how to prevent similar issues:
For remediation best practices, please also refer to OWASP remediation guidelines. More information about coordinate and responsible disclosure on Open Bug Bounty is available here.
DISCLAIMER: Open Bug Bounty is a non-profit project, we never act as an intermediary between website owners and security researchers. We have no relationship or control over the researchers. Our role is limited to independent verification of the submitted reports and proper notification of website owners by all reasonably available means.
washingtonpost.com
Website Overview and Rating
| SSL/TLS Server Test: | A View Results |
| Web Server Security Test: | A View Results |
| Malware Test: | Click here |
| Domain Health Report: | Click here |
Latest Submissions
| OBB-ID | Reported by | Status | Reported on |
|
patched
|
18.10.2018
|
||
|
patched
|
25.05.2018
|
||
|
patched
|
19.10.2017
|
||
|
patched
|
09.09.2017
|
||
|
patched
|
29.08.2017
|
||
|
patched
|
24.08.2017
|
||
|
patched
|
16.07.2017
|
||
|
patched
|
14.06.2017
|
||
|
patched
|
25.05.2017
|
||
|
patched
|
06.05.2017
|
||
|
unpatched
|
25.03.2017
|
||
|
patched
|
31.12.2016
|
||
|
patched
|
25.12.2016
|
||
|
patched
|
19.05.2016
|
||
|
patched
|
03.05.2016
|
||
|
patched
|
22.09.2015
|
||
|
patched
|
18.06.2015
|
||
|
patched
|
30.03.2015
|
||
|
patched
|
28.06.2014
|
||
|
patched
|
26.06.2014
|

 Platform update: please use our
Platform update: please use our 




