Table of Contents
- About Open Bug Bounty
- Open Bug Bounty for Security Researchers
- Open Bug Bounty for Website Owners
- Project History
- Coordinated and Responsible Disclosure
- Safe and Non-Intrusive Testing
- Submission and Verification Process
- Public and Private Submissions
- Bounties and Awards
- Good Faith and Ethics
- Available Integration
- Frequently Asked Questions
About Open Bug Bounty
Open Bug Bounty project enables website owners to receive advice and support from security researchers around the globe in a transparent, fair and coordinated manner to make web applications better and safer for everyone’s benefit.
Among other recognitions, the Open Bug Bounty project was named among the Top 5 Bug Bounty programs of 2021 by The Hacker News and among the Top 6 Bug Bounty programs of 2022 by the InfoSec Institute.
Open Bug Bounty for Security Researchers
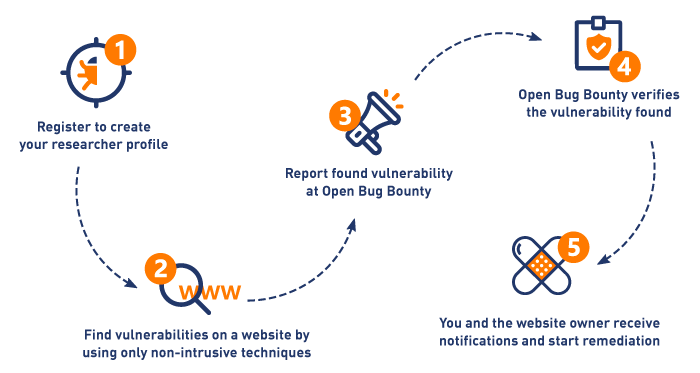
Open Bug Bounty for Website Owners
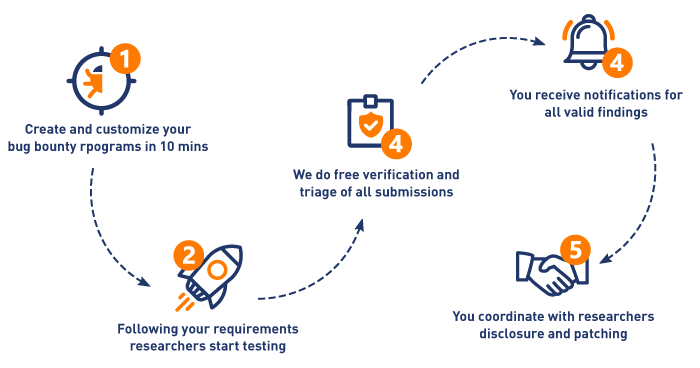
Project History
Started by a group of independent security researchers in June 2014, Open Bug Bounty is a non-profit platform designed to connect security researchers and website owners in a transparent, respectful and mutually valuable manner. Our purpose is to make the Web a safer place for everyone’s benefit.
We have no financial or commercial interest in the project. Moreover, we pay hosting expenses and web development costs from our pocket, and spend our nights verifying new submissions.
Coordinated and Responsible Disclosure, ISO 29147
Open Bug Bounty’s coordinated vulnerability disclosure platform allows any security researcher reporting a vulnerability on any website as long as the vulnerability is discovered without any intrusive testing techniques and is submitted following responsible disclosure guidelines.
The role of Open Bug Bounty is limited to independent verification of the submitted vulnerabilities and proper notification of website owners by all available means. Once notified, the website owner and the researcher are in direct contact to remediate the vulnerability and coordinate its disclosure. At this and at any later stages, we never act as an intermediary between website owners and security researchers.
Open Bug Bounty platform follows ISO 29147 standard's (“Information technology -- Security techniques -- Vulnerability disclosure”) guidelines of ethical and coordinated disclosure. As per the standard, Open Bug Bounty pursues the following goals of vulnerability disclosure:
 | ensuring that identified vulnerabilities are addressed; |
 | minimizing the risk from vulnerabilities; |
 | providing sufficient information to evaluate risks from vulnerabilities to their systems; |
 | setting expectations to promote positive communication and coordination among involved parties. |
As a global vulnerability disclosure Coordinator, Open Bug Bounty also serves the following non-profit roles as suggested by ISO 29147 in the vulnerability disclosure process:
 | act as a trusted liaison between the involved parties (researchers and website owners); |
 | coordinate responsible disclosure; |
 | enable communication between the involved parties; |
 | provide a forum where experts from different organizations can collaborate. |
Risk level of the submitted vulnerabilities is scored using Common Vulnerability Scoring System (CVSS).
Submitted vulnerabilities are classified by Common Weakness Enumeration (CWE).
Safe and Non-Intrusive Testing
We only accept Cross-Site Scripting, CSRF and some other vulnerabilities that figure among the most common web application vulnerabilities today.
When reporting GDPR PII exposure, we do not store the PII but the blurred screenshot after verifying the vulnerability.
The proper process of testing for these vulnerabilities is harmless and cannot damage a website, database, server or related infrastructure. We do not accept vulnerabilities that can, or are intended to, harm a website, its data or related infrastructure.
Open Bug Bounty prohibits reporting of vulnerabilities that were detected by vulnerability scanners and other automated tools that may impact website performance or cause any other negative impact.
Submission and Verification Process
Once a vulnerability is reported and confirmed, we immediately send a security alert to the website owner following ISO 29147 guidelines, as well as to specific security contacts provided by the researcher. We strongly encourage security researchers to ensure reliable notification of the website owner for every submission.
Security researchers can publicly disclose technical details of the vulnerabilities they report if they wish to do so. However, in order to give website owners appropriate time to remediate the vulnerability without putting any undue pressure on them, technical details can be disclosed only in 90 days from the original submission, or in 30 days if the vulnerability is patched..
To avoid spam and other potential inconvenience, we limit reporting to one vulnerability per domain per 24 hours. Every recipient of notifications sent can unsubscribe from any further notifications.
Open Bug Bounty: Public and Private Submissions
Security researcher can choose how to report vulnerabilities. Website owners with bug bounties on Open Bug Bounty can limit submissions only to private ones:
Public Submission
Once verified, we send notifications, without disclosing any technical details of the vulnerability, to:
 | Verified website owner (condition to exiting bug bounty) |
 | Generic security emails |
 | Emails suggested by ISO 29147 |
 | Emails provided by the researcher |
 | Security emails found on the website (if any) |
 | Website owner accounts in social networks. |
A public web page dedicated to the vulnerability will be automatically created, however no technical details will be displayed on it. At this stage, a website owner, administrator or security company in charge of the website security can contact the researcher directly and proceed to coordinated disclosure.
Private Submission
After verification, the vulnerability will be available on a secret hyperlink known only to the security researcher and website owner if s/he runs a bug bounty on Open Bug Bounty. The vulnerability will not be used in any detailed statistics or lists on the website (the total counter of submissions will increment). Private submission serves to (a) provide flexible Vulnerability Disclosure Program to website owners, and (b) to report vulnerabilities on websites running external bug bounty program, but refusing to reward a researcher for a reason. Our independent and impartial verification proves that the vulnerability existed at a precise timestamp, giving a fair discovery credit to the researcher. Same as public submissions, private submission can be disclosed by the researcher on the aforementioned conditions.
For both types of submissions, security researcher can delete the vulnerability submission at any time before public disclosure of the vulnerability details. However, once disclosed, the submission can no longer be deleted to prevent undue pressure on the researchers. We never remove any information about vulnerabilities for political or business reasons.
Bounties and Awards
A website owner can express a gratitude to a researcher for reporting vulnerability in a way s/he considers the most appropriate and proportional to the researcher's efforts and help.
As a matter of example, Google pays from $7,500 to $100 per XSS vulnerability submitted by security researchers. But Google is Google, you may adjust your remuneration range to any amounts comfortable for you.
We encourage website owners to say at least a “thank you” to the researcher or write a brief recommendation in the researcher’s profile. There is, however, absolutely no obligation or duty to express a gratitude in any manner. We promote positive, constructive and mutually respectful communications between website owners and security researchers.
On the platform, researchers get various honorary badges for quality of their submissions and the number of websites they helped to secure. We always encourage quality, not quantity of submissions.
Bug Bounty owners who refuse providing promised remuneration or award for a valid submission may have their Bug Bounty program permanently suspended.
Good Faith and Ethics
We have a zero tolerance policy for any unethical or unlawful activities.
We always encourage the researchers to be respectful, responsive and polite, to provide website owners with all reasonable help and assistance.
If a researcher violates the enacted standards of ethics and good faith including but not limited to:
- demanding remuneration to delete a submission
- demanding remuneration to disclose vulnerability details
such submissions will be immediately deleted from our platform. Website owners running bug bounties and not rewarding the researchers as stipulated in their bug bounty description may have their bug bounty deleted from our platform.
Available Integration
For website owners, we provide vulnerability data export option to the following SDLC, DevOps and bug tracking systems:
 |
 |
 |
 |
Frequently Asked Questions
Have any questions? Please read our Frequently Asked Questions designed for you.

 Platform update: please use our
Platform update: please use our 




